Let me start with the two questions.
1. Would you install a wireless access point with open access to the public on your home network?
2. Would you freely provide an Ethernet (network) port for strangers to plug into out in your yard?
I would hope that in both cases you answered with a resounding NO.
The security of you home network and all the private information it has along with usually family photos and other important things should be paramount in your mind when deciding how to set up your lighting network.
I highly recommend as best practice for non technical people a physically separated network be setup and used. This provides the comfort that your home network is safe from physical intrusion by a hacker.
Buy the separate network switch to plug in all your controllers, Pi's, BBB's, projectors, show computers.
This does make it a little more complex for IP addresses as you will need to run manually fixed IP addresses for all devices.
The lack of DHCP can be quite cheaply solved by buying a cheap Wireless access point and using it to provide DHCP service to you separate network, you can turn off the Wireless for full security or use it for management access from your home PC/Laptop, just ensuring that the WAP does not route multicast traffic out.
Reading the above paragraph, with the prolific use of laptops and wireless in general this overcomes the immediate objection that you can't access this from you home network.
The key message though is we spend thousands every year on lights and controllers but seem to baulk at spending less that $100 to set up a separate network as it is often touted as being "too hard".
The diagram give an example simple setup
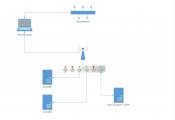
1. Would you install a wireless access point with open access to the public on your home network?
2. Would you freely provide an Ethernet (network) port for strangers to plug into out in your yard?
I would hope that in both cases you answered with a resounding NO.
The security of you home network and all the private information it has along with usually family photos and other important things should be paramount in your mind when deciding how to set up your lighting network.
I highly recommend as best practice for non technical people a physically separated network be setup and used. This provides the comfort that your home network is safe from physical intrusion by a hacker.
Buy the separate network switch to plug in all your controllers, Pi's, BBB's, projectors, show computers.
This does make it a little more complex for IP addresses as you will need to run manually fixed IP addresses for all devices.
The lack of DHCP can be quite cheaply solved by buying a cheap Wireless access point and using it to provide DHCP service to you separate network, you can turn off the Wireless for full security or use it for management access from your home PC/Laptop, just ensuring that the WAP does not route multicast traffic out.
Reading the above paragraph, with the prolific use of laptops and wireless in general this overcomes the immediate objection that you can't access this from you home network.
The key message though is we spend thousands every year on lights and controllers but seem to baulk at spending less that $100 to set up a separate network as it is often touted as being "too hard".
The diagram give an example simple setup



